
Common Excel Formulas
A handy reference of frequently used Excel formulas and their functions to help you perform calculations, text manipulation, and lookups efficiently.
Learn how to convert almost any file using the all in one file conversion app

A handy reference of frequently used Excel formulas and their functions to help you perform calculations, text manipulation, and lookups efficiently.
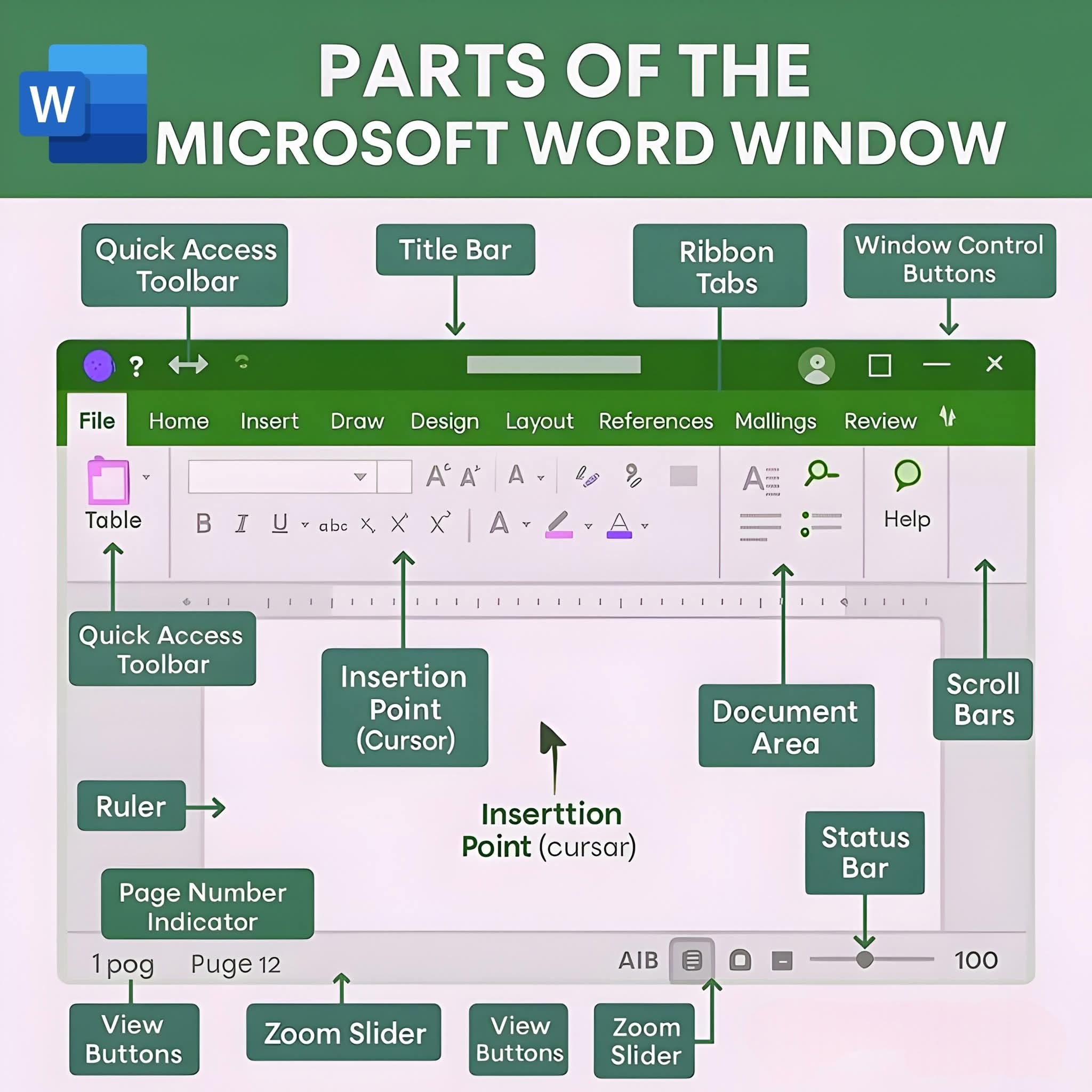
Understanding the key components of the Microsoft Word window helps you navigate and use the program efficiently.
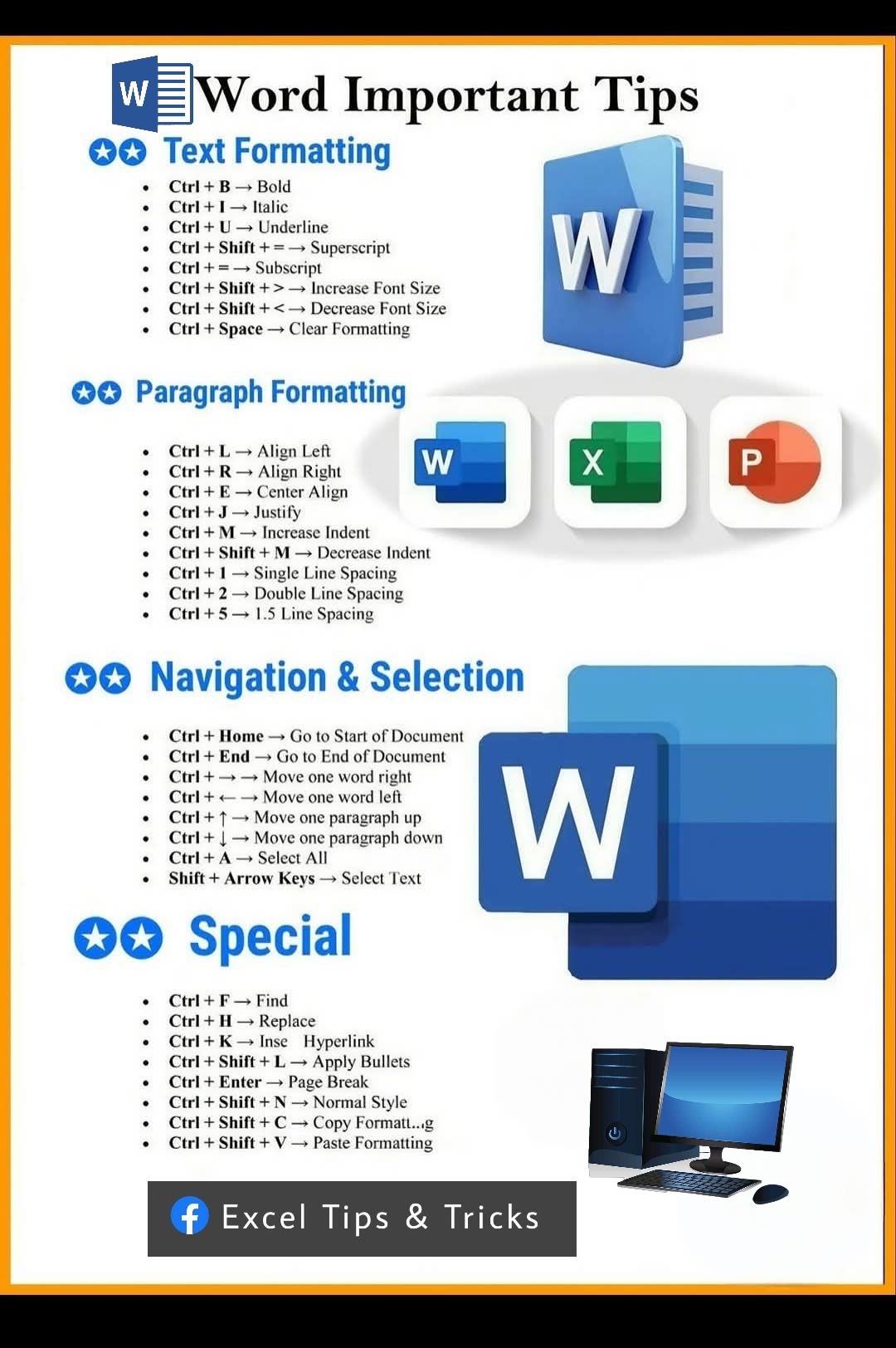
These keyboard shortcuts help you format text, manage paragraphs, navigate documents, and perform special actions efficiently in Word.
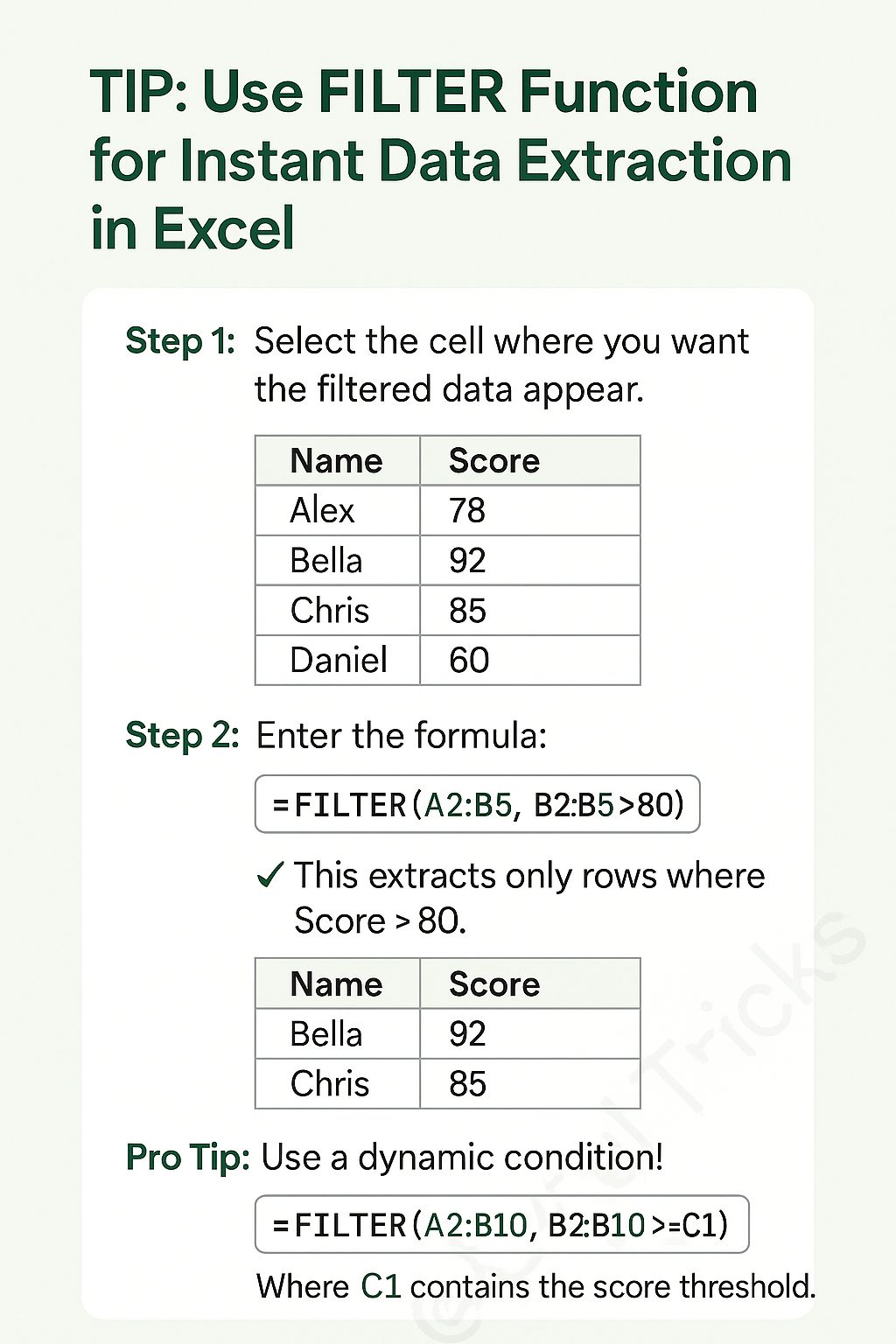
The FILTER function allows you to extract specific data from a table based on given criteria.

These keyboard shortcuts help you manage workbooks and worksheets efficiently, giving quick access to common tasks in Microsoft Excel.
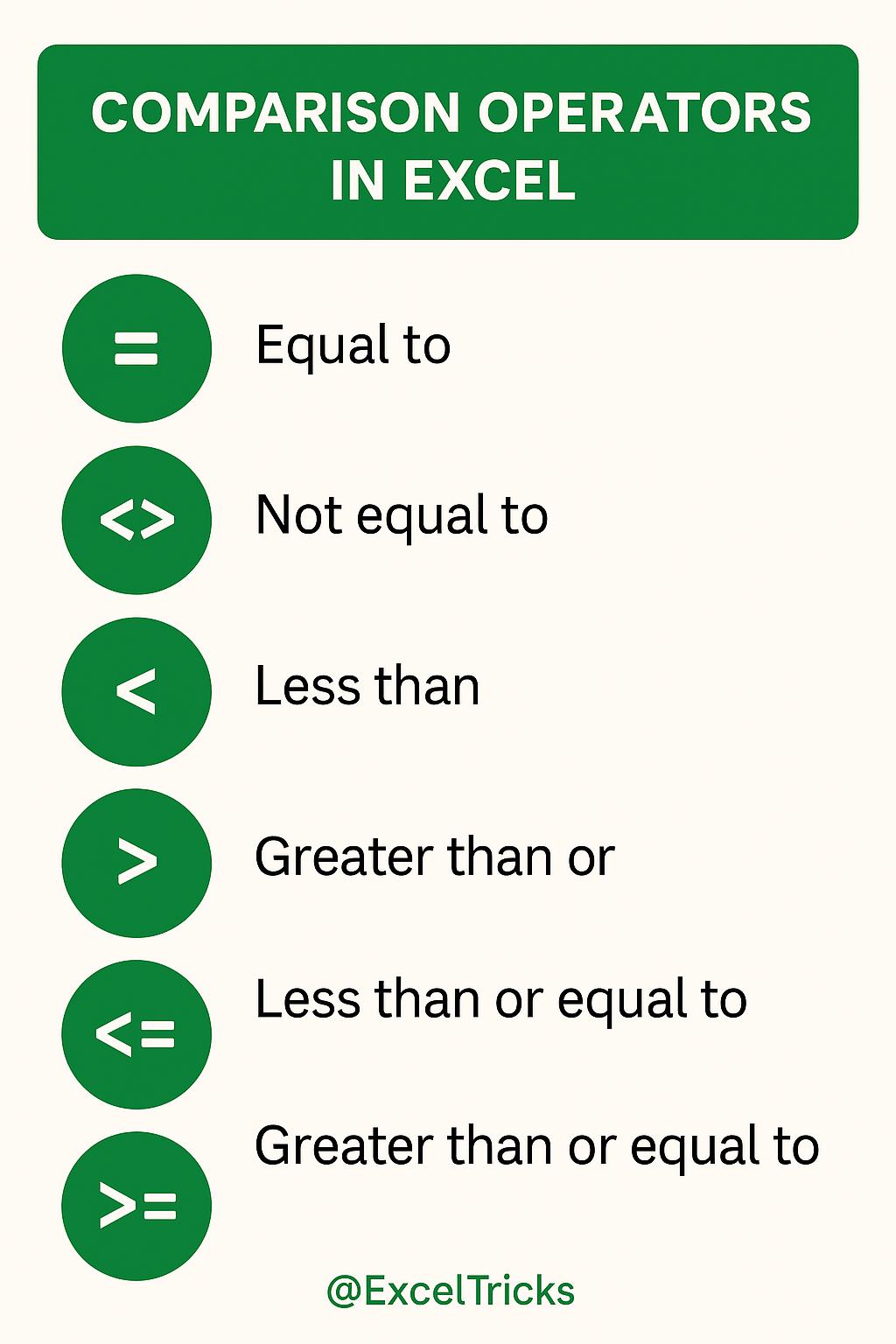
Comparison operators are used in Excel formulas to compare two values, and the result is either TRUE or FALSE. They are essential for creating logical tests within functions like IF.

Combine the IF and OR functions to test multiple conditions in a spreadsheet program.
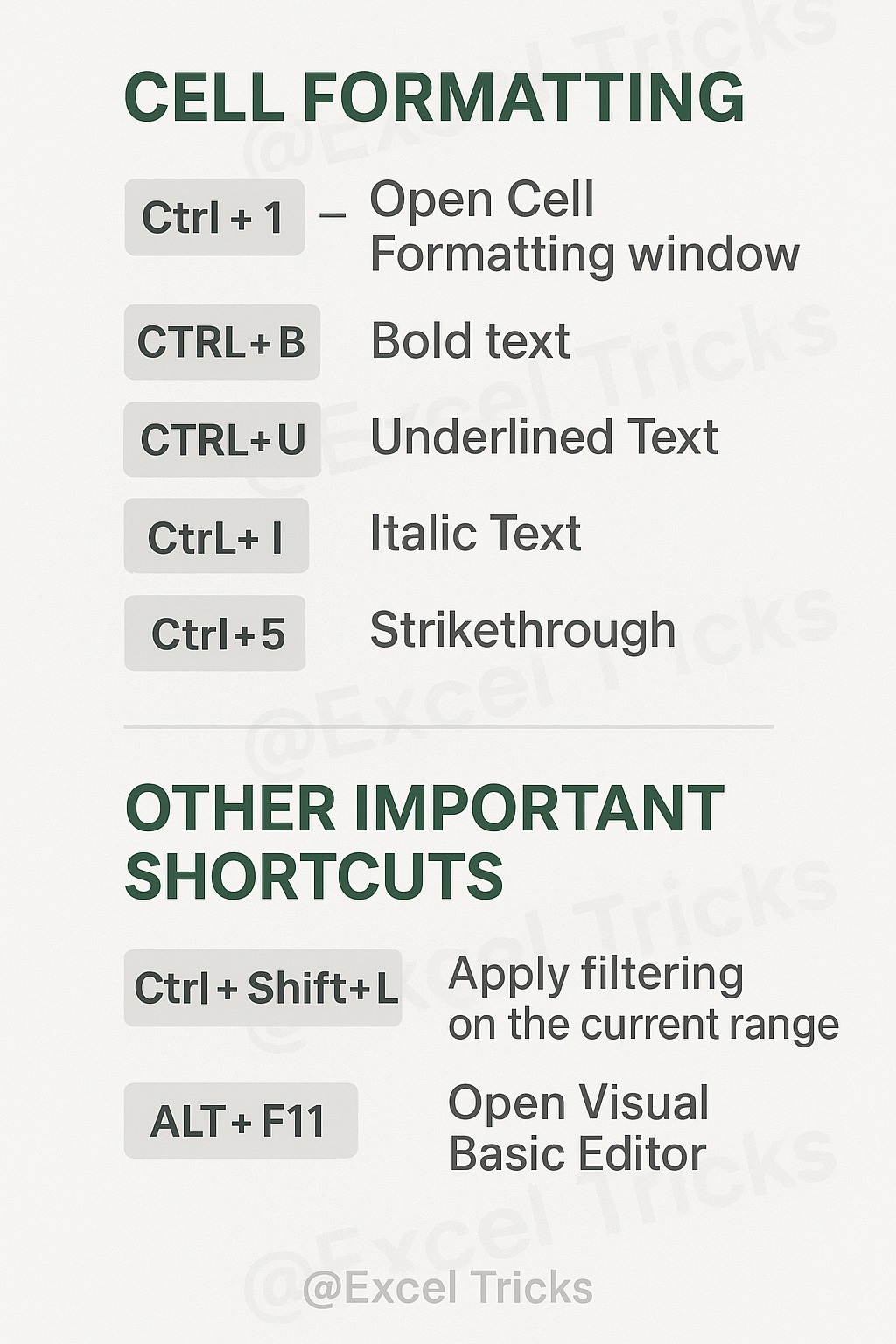
Mastering keyboard shortcuts can dramatically speed up your workflow in Excel. These shortcuts are divided into two main categories: Cell Formatting and Other Important Shortcuts.

A sparkline is a small chart located inside a single cell that displays data trends, such as seasonal ups and downs, cycles, or highs and lows. They are best placed near the data they represent. How to Add a Sparkline
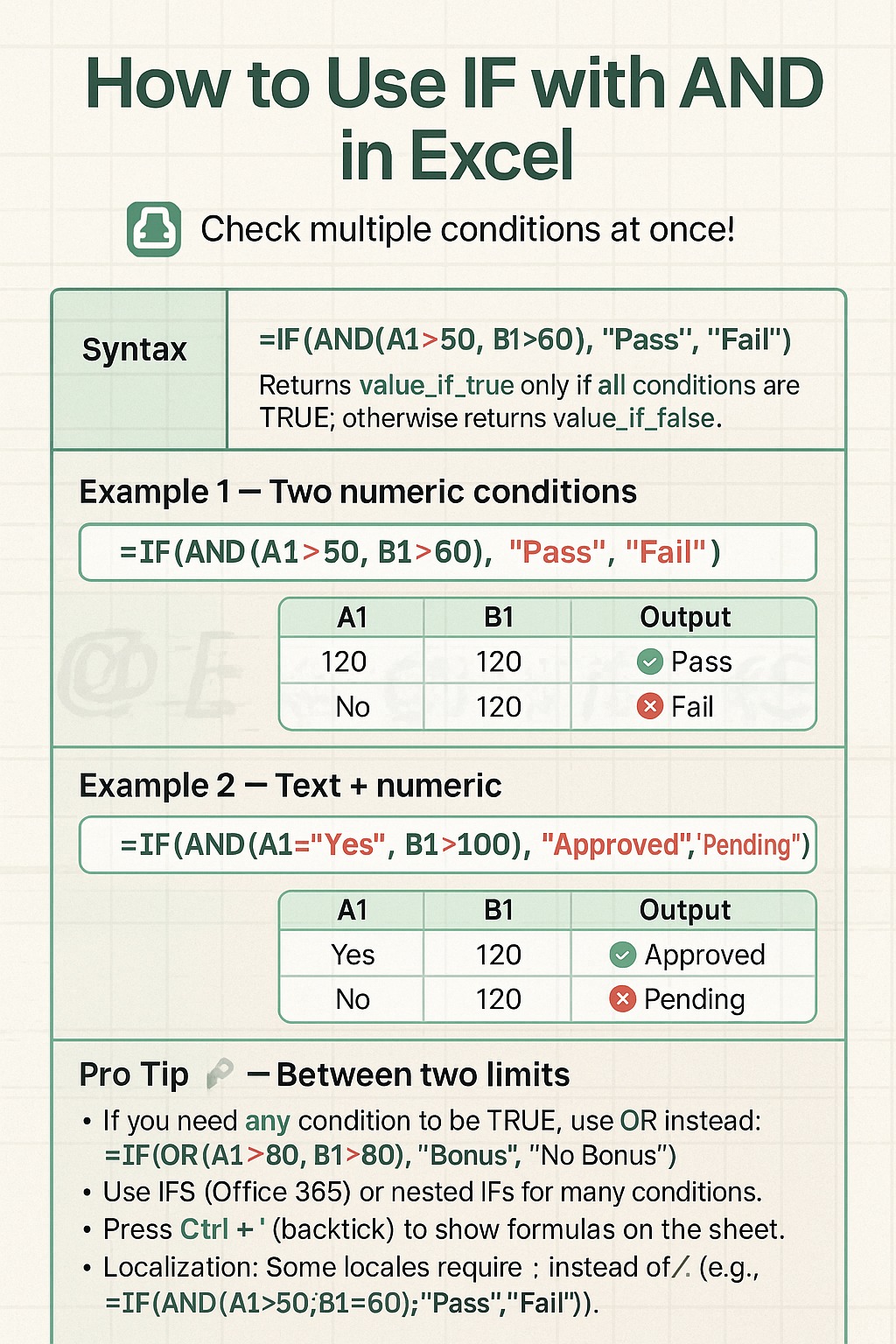
Want to test several conditions in a single formula? Combine the IF and AND functions!