A new strain of ransomware has emerged that is targeting players across about 40 online games, seemingly aiming at a younger demographic of computer users.
Ransomware is a type of malicious software that encrypts the files on an infected machine. Once the files are locked, the attackers demand a ransom for the private key needed to unlock them. If the ransom is not paid within a set timeframe, the decryption key is destroyed, leaving the files inaccessible.
The malware was first highlighted by Bleeping Computer, a forum specializing in technical support and user guidance, which has quickly become a trusted source for information on ransomware and encryption threats. Bleeping Computer has named this malware TeslaCrypt, while security firm Bromium released an independent report, calling it a new variant of CryptoLocker. Fabian Wosar from Emsisoft is credited with initially discovering TeslaCrypt.
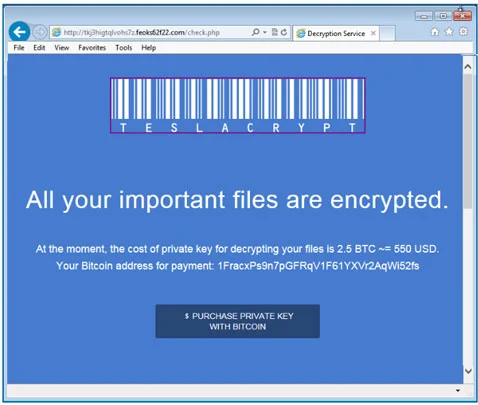
According to Bleeping Computer, TeslaCrypt focuses on game-related files and platforms such as RPG Maker, League of Legends, Call of Duty, Dragon Age, StarCraft, Minecraft, World of Warcraft, World of Tanks, and other popular online titles. This approach is different from earlier ransomware campaigns, which usually targeted documents, photos, videos, and other common files. TeslaCrypt uses AES encryption, making gaming files inaccessible without the private key. Victims are asked to pay $500 via Bitcoin or $1,000 through a PayPal My Cash card to retrieve the key.
While Bleeping Computer led the reporting, Bromium added details on how TeslaCrypt spreads. Unsurprisingly, attackers are distributing it via the Angler Exploit Kit, a pre-packaged tool designed to exploit security flaws in computer systems. Similar to software-as-a-service, cybercriminals can "license" these kits to infect victims’ machines.
Exploit kits make it easy to deploy malware. Previously, BlackHole was the dominant kit, but it lost popularity after its creator stopped development and was arrested in Russia. Since then, Angler has taken its place, incorporating the latest zero-day vulnerabilities along with known exploits.
A new piece of #ransomware called #TeslaCrypt is targeting #gamers
Tweet
After infection, TeslaCrypt changes the victim’s desktop background with a warning that files are encrypted, along with instructions on how to pay for the private key. Users are prompted to download the Tor Browser to access a hidden service where the attackers provide guidance for payment and decryption. A deadline is included; once passed, the key is destroyed and files become irrecoverable.
The warning closely resembles that of CryptoLocker, which may explain Bromium’s view that the two are connected. While technical similarities are limited, TeslaCrypt seems to leverage the notoriety of CryptoLocker’s name.
ImgConverter Daily strongly advises against paying for the private key, as doing so supports the scam. Regular backups are the most reliable protection. Additionally, using a robust antivirus product such as ImgConverter Internet Security or ImgConverter Total Security, which include features like System Watcher, can help defend against cryptoware threats.
It is also crucial to keep your operating system, software, applications, and browsers up-to-date, as most exploit kits target known vulnerabilities that have already been patched.
As we’ve mentioned before, crypto ransomware remains a serious threat. Regularly backing up your data is essential. Attackers are becoming more sophisticated in both spreading infections and convincing users to pay for recovery. With more devices connecting to the internet than ever before, the risk is only increasing.